With FIDO coming to replace passwords in applications, CPaaS vendors are likely to decline in 2FA revenues.

2FA revenue has always lived on the premise that passwords are broken. I’ve written about this back in 2017:
Companies are using SMS for three types of services these days:
1. Security — either through two-factor authentication (2FA), for signing in to services; or one-time password (OTP), which replaces the need to remember a password for various apps
2. Notifications for services — these would be notifications that you care about or that offer you information, like that request for feedback or maybe that birthday coupon
3. Pure spam — businesses just send you their unsolicited crap trying to get you to sign up for their services
Spam is spam. Notifications are moving towards conversations on social networks. And the security SMS messages are going to be replaced by FIDO. Here’s where we’re headed.
Let’s take this step by step.
Table of contents
Passwords and the FIDO Alliance
Passwords are the bane of our modern existence. A necessary evil.
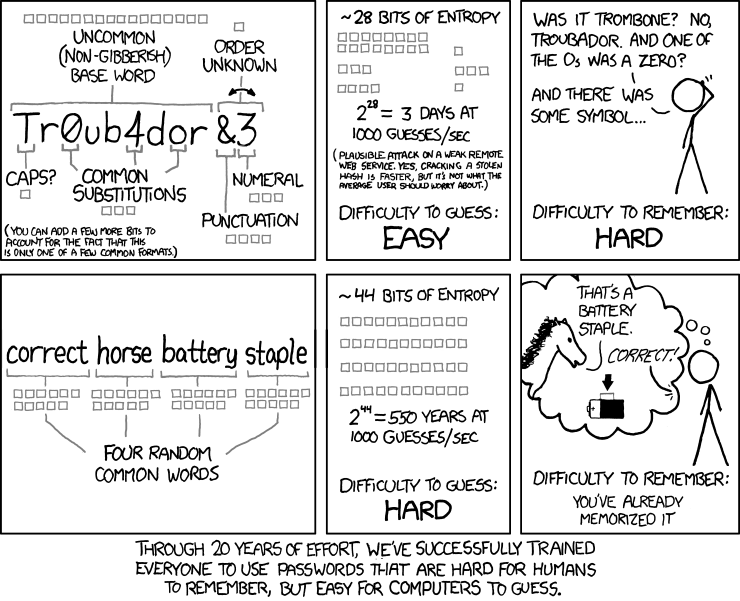
To do anything meaningful online (besides reading this superb article), you need to login or identify yourself against the service. Usually, this is done by a username (email or an identity number most likely) and a password. That password part is a challenge:
- It needs to be something you remember (=know)
- But you can’t use it on more than one site. If you do, and that site is hacked, then your data on other sites is going to be exposed
- And that password needs to be non-simple. So it can’t be easily guessed
- So 8 characters or more. Upper and lower case. A digit or two or three please. Maybe a special character to boot
- Oh – and please change it every 3 or 6 months because… security
I use a password manager to handle my online life. My wife uses the “forgot my password” link all the time to get the same results.
It seems that whatever was tried in the passwords industry has failed in one way or another. Getting people house trained on good password practices is just too damn hard and bound to failure (just like trying to explain to people not to throw facial tissue down the toilet).
Experts have since pushing for a security model that authenticates a user with multiple “things”:
- Something you know (=password)
- Something you own (=smartphone or security key)
- Something you are (=biometrics)
Smartphones today are something you own and they offer something you are by having fingerprint ID and face ID solutions baked into them. That last piece is the password.
Enter FIDO.
FIDO stands for Fast IDentity Online.
Here’s the main marketing spiel of the FIDO Alliance:
The FIDO Alliance seems to have more members than it has views on that YouTube video (seriously).
By their own words:
The FIDO Alliance is working to change the nature of authentication with open standards that are more secure than passwords and SMS OTPs, simpler for consumers to use, and easier for service providers to deploy and manage.
So:
- Open standards
- More secure than passwords and SMS OTPs
- Simpler for consumers to use
- Easier to deploy and manage
What more can you ask for?
Well… for this standard to succeed.
And here is what brought me to write this article. The recent announcement from earlier this month – Apple, Google and Microsoft all committing to the FIDO standard. They are already part of FIDO, but now it is about offering easier mechanisms to remove the need for a password altogether.
If you are reading this, then you are doing that in front of an Apple device (iPhone, iPad or MacOS), a Google one (Android or Chrome OS) or a Microsoft one (Windows). There are stragglers using Linux or others, but these are tech-savvy enough to use passwords anyways.
These devices are more and more active as both something you own and something you are. My two recent laptops offer fingerprint biometric identification and most (all?) smartphones today offer the same or better approaches as well.
I long waited for Google and Apple to open up their authentication mechanisms in Android and iOS to let developers use it the same way end users use it to access Google and Apple services – when I login to any Google connected site anywhere, my smartphone asks me if that was me.
And now it seems to be here. From the press release itself:
Today’s announcement extends these platform implementations to give users two new capabilities for more seamless and secure passwordless sign-ins:
1. Allow users to automatically access their FIDO sign-in credentials (referred to by some as a “passkey”) on many of their devices, even new ones, without having to re-enroll every account.
2. Enable users to use FIDO authentication on their mobile device to sign in to an app or website on a nearby device, regardless of the OS platform or browser they are running.
So… no need for passwords. And no need for 2FA. Or OTP.
FIDO is going to end the farce of using 2FA and OTP technologies.
2FA: a CPaaS milking cow
2FA stands for Two Factor Authentication while OTP stands for One Time Password.
With 2FA, you enter your credentials and then receive an SMS or email (or more recently Whatsapp message) with a number. You have to paste that number on the web page or app to login. This adds the something you own part to the security mechanism.
OTP is used to remove the password altogether. Tell us your email and we will send you a one time password over SMS (or email), usually a few digits, and you use that to login for just this once.
2FA, OTP… the ugly truth is that it is nagging as hell to everyone. Not only users but also application developers. The devil is always in the details with these things:
- How do you send an SMS message?
- What happens if the SMS or email isn’t received? Is there a retry mechanism?
- Can the user complain if it doesn’t work to get things resolved?
- Who takes care of internationalization of these messages?
- …
The list goes on. So CPaaS vendors have gone ahead and incorporated 2FA specific solutions into their bag of services. Twilio even acquired Authy in 2015, a customer, just to have that in their offerings at the time.
The great thing about 2FA (for CPaaS vendors), is that the more people engage with the digital world, the more they will end up with a 2FA or OTP SMS message. And each such message is a minor goldmine: A single SMS on Twilio in the US costs $0.0075 to send. A 2FA transaction will cost an additional $0.09 on top of it.
Yes. 2FA services bring great value. And they are tricky to implement and maintain properly at scale. So the price can be explained. But… what if we didn’t really need 2FA at all?
The death of 2FA

Putting one and one together:
Apple, Google and Microsoft committing to FIDO and banishing passwords by making their devices take care of something you know, something you own AND something you are means that users will not need to identify themselves in front of services using passwords AND they won’t be needing OTP or 2FA either.
The solution ends up being simpler for the user AND simpler for the service provider.
Win Win.
Unless you are a CPaaS vendor who makes revenue from 2FA. Then it is pure loss.
What alternatives can CPaaS vendors offer?
At first step, the “migration” from “legacy” 2FA and OTP towards Apple/Google’s new and upcoming FIDO solution. Maybe a unified API on top of Apple and Google, but that’s a stretch. I can’t see such APIs costing $0.09 per authentication. Especially if Apple and Google do a good job at the developer tooling level for this.
* I removed Microsoft closer to the end here because they are less important for this to succeed. They are significant if this does succeed in making it even simpler on laptops so one won’t have to reach for his phone to login when on a laptop.
The future of CPaaS
5 years ago, back in that 2017 article, I ended it with these words:
Goodbye SMS, It’s Time for Us to Move On
Don’t be fooled by the growth of 2FA and application-to-person (A2P) type messages over SMS. This will have a short lifespan of a few years. But five to 10 years from now? It will just be a service sitting next to my imaginary fax machine.
We’re 5 years in and the replacements of SMS are here already.
- Social truly is starting to replace SMS notifications with long lived conversations, augmented with the surge of chatbots everywhere
- 2FA and OTP are now threatened by FIDO to be replaced simply by the fact that you own a smartphone
All that revenue coming to CPaaS from SMS is going to go elsewhere. Social omnichannel introduced by CPaaS vendors will replace that first chunk of revenue, but what will replace the 2FA and OTP? Can CPaaS vendors rely on FIDO and build their own business logic on top and around it for their customers?
It seems to me revenue will need to be found elsewhere.

Interested in learning more about the future of CPaaS? Check out my ebook on the topic (relevant today as it was at the time of writing it).

Fido keys are here since a long time and regular consumers have no clue what they are. I believe 2fa over sms (and voice calls) still have years ahead, also considering entreprises are slow in changing their 2fa implementations.
For average end users and consumers, I believe sms based 2fa more likely to be replaced by authenticator apps (Google authenticator, ms authenticator, duo.,…) and/or in-app notifications.
Thanks Fred!
I think this will go like Blackberry and the iPhone – only slower. 2FA/OTP has peaked or will peak soon. Because once FIDO comes to devices and enabled for application authentication it dilutes the need for passwords and 2FA/OTP while improving security. And you don’t ask users – you “force” it on them. It will also probably cost less to maintain than 2FA (no SMS).
Authenticator apps are a nag. I am using them and grumbling about it all the time. A necessary evil just like 2FA.
And yes, 2FA over SMS has years until it dies, but I think it can now be considered a legacy technology with a death date.