Yes.
Don’t you just LOVE it when a question can be answered with a simple Yes?

In recent years, we’ve seen a lot of hysteria going on around WebRTC security. Mainly it being unsafe to use. So much so, that there are tutorials out there explaining how to disable it in every conceivable browser out there.
This reminds me all of the past (and present?) hysteria around running JavaScript code inside the browser – and again – how to disable it.
If you are developing a WebRTC application AND you care about the security of your service and the privacy of your users, make sure to review my WebRTC Security Checklist.
If you are after a more thorough look at the topic, make sure to also read this article: Everything you need to know about WebRTC security.
Why is WebRTC Perceived as Dangerous?

WebRTC is a real time communication technology that is embedded in the browser. It can access your camera and your microphone as well as share the contents of your screen. As such, it enables a browser (and web developers) access to a lot more resources on the device of an end user.
This boils down to two main risks:
- Your data can be stolen by nefarious people
- Your privacy can be breached by knowing more about your device
1. Your data can be stolen by nefarious people
Here are a few scary ideas:
- If I can access your microphone, I’ll be able to record all of your conversations
- If I can access your camera, I’ll be able to snoop on you. Maybe take a nice recording of your intimate moments
- If I can access your screen remotely, I’ll be able to record what you’re doing. Maybe even control your mouse and keyboard remotely while at it?
With all the goodness WebRTC brings, who wants to be spied on by his own device?
Now, that said, we also need to understand two things here:
- The browser isn’t the only game in town to gaining this access to your data and actions
- There are measures put in place to limit the ability to conduct in such activities
2. Your privacy can be breached by knowing more about your device
This one I guess is mostly about tracking you over the internet. Which is what ad networks are doing most of the time.
WebRTC gives access to more elements that are unique, which makes fingerprinting of the device (and you) a lot more accurate. Or so they say.
The main concern here are around the exposure of private IP addresses to web servers. There are many out there who see these “IP leaks” as a serious threat. for most of humanity, I believe it isn’t, which is why I’ll gladly publish my private IP address here: 10.0.0.9.
There are other, more nuanced ways in which WebRTC can be used for fingerprinting, such enumerating the device list as part of your device’s unique identity. Which is a concern, until you review the accuracy of fingerprinting without even using WebRTC. Here are two resources for you to enjoy:
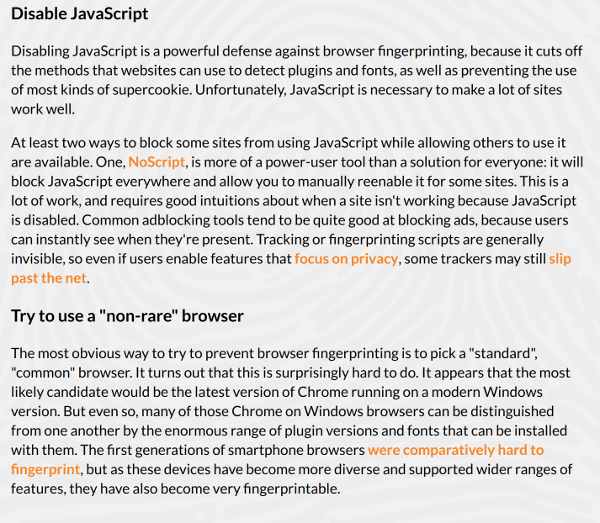
- Panopticlick – EFF’s fingerprinting check up ad research. If you are not unique – comment below – I have a feeling your browser is as unique as mine. Their TL;DR? Disable JavaScript (which will be too much work) or use a more “common” browser. I am NOT making this up:
- Fingerprintjs2 – one of the many libraries available to fingerprint your browser. It doesn’t use WebRTC, although there’s an “intent” in there to add support to it
In this area, Apple with their new WebRTC support in Safari is leading the way in maintaining privacy. You can read about it in a recent article in the WebKit blog. Look specifically on the sections titled “ICE Candidate Restrictions” and “Fingerprinting”.
Why is WebRTC the Safest Alternative?

If you are a developer looking for a real time communications technology to use in your application, or you are an IT person trying to decide what to deploy in your company, then WebRTC should be your first alternative. Always.
Here’s why.
1. Browser vendors take care security seriously
There are 4 major browser vendors: Apple, Google, Microsoft and Mozilla
All of these vendors are taking care of security and patching their browsers continuously. In some cases, they even roll out new versions at breakneck speeds of 6-8 weeks, with security patches in-between.
If a security threat is found, it gets fixed fast.
While many other vendors can say that they are fixing and patching security threats fast – do they deploy them fast? Do they have the means to do so?
Since browsers get updated and upgraded so frequently, and to hundreds of millions of users, getting a security patch to the field happens rather fast. Philipp Hancke showed and explained some Here are some browser upgrade stats last year. This is from real users conducting Whereby sessions. I asked him to share a more recent graph, and here’s what they’ve had in the last two large browser version cycles for Chrome:
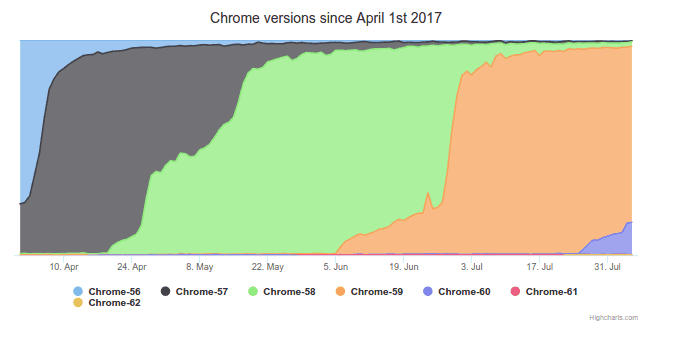
Look at the point in time when each Chrome version got ramped up from less than 30% to over 80% in a span of a couple of days. Chrome 59 is especially interesting. Also note that there are at most 2 versions of Chrome out there with over 95%+ of use. Since they routinely do it, patching and deploying security issues is “easy”.
The only other vendors who can roll out and deploy patches so fast? Operating system vendors (again we end up with Apple, Google and Microsoft), and application developers, through mobile app stores (which sums up to Apple and Google).
Nothing comes close to it.
Takeaway: Assume there will be security breaches or at the very least the need to patch security issues. Which means you should also plan for upgrade policies. Browsers are the best at upgrading these days.
2. You don’t need to redeploy the client software
Lets face it – most users don’t disable the automatic update policy of their browsers. If you’re even remotely interested in security, you shouldn’t disable automatic update policies of ANYTHING.
Manual updates bring with them a world of pain:
(a) When do you upgrade?
Here’s the thing.
How do you know an upgrade is in order? Are you on the list of threat alerts of all the software and middleware you are using in your company? Once a threat is announced and a patch is available – do you immediately upgrade?
When we leave this decision to a human, then he might just miss the alert. Or fail to upgrade. Or decide to delay. Just because… he’s human.
Most software can get updated, but usually won’t do it automatically or won’t do it silently. And automation in this area that is done externally, such as the Kaspersky Software Updater. It works, but up to a point and it also adds another headache to contend with and manage.
If a browser does that for you freely, why not use it?
(b) What if this fails?
Did you ever get a software update to fail?
What about doing that in a company with 100+ employees?
If software fails to update 1% of the time, it means that every time you update something – someone will complain or just fail to update, making you revert back to a manual process.
There are tons of reasons why these processes fail, and most are due to the fact that we all have different firmware, software and device drivers on our machines (see fingerprinting above). This fact alone means that if a software isn’t running on millions of devices already, it will fail for some. I’ve seen this too many times when the company I worked for developed a plugin for browsers.
Anyone not using WebRTC and deploying via software installation will cause you grief here. If this is only in front of employees, then maybe that’s fine. But often times this is also with end user devices – and you don’t want to mess there.
Browser upgrades will fail a lot less often, so better use that and just make use of WebRTC instead of rolling your own proprietary solution.
(c) What about edge cases?
You can’t control your employees and their whereabouts for your upgrades.
People working from home.
People traveling abroad.
People using BYOD and… not having tight enterprise policies on their own home laptop.
If you want less headache in this department, then again – using WebRTC will give you peace of mind that security patches get updated.
Why?
Look at it this way, the engine of WebRTC will always stay secure when you rely on browser and browser updates.
You have control over the backend (or rely on a cloud service provider with an SLA you are paying for exactly for this reason). The backend gets updated for security patches all the time (or as much as you care). The browsers get updated automatically so you can think less about it.
Using proprietary software or legacy VoIP vendor software means you’ll need to patch both backend and client software. This is harder to do and maintain – and easier to miss.
3. WebRTC has inherent security measures in place
This should probably be the first reason…
One thing you hear many complain about is questioning why WebRTC is always encrypted. Somehow, developers decided that sending media in the clear is a good thing. While there might be some reasons to do that, most of them are rather irrelevant for something like WebRTC, meant to be used on unmanaged networks.
WebRTC took the approach of placing its security measures first. This means:
- There’s no way send media in the clear. Everything is always encrypted. In other VoIP solutions, you can configure encryption on and off (if encryption is even there)
- There’s no way to use WebRTC in websites that aren’t served over HTTPS. This means WebRTC forces developers to use secure connections for signaling – and for the whole site. And no. Using iframes won’t work either
- Users are asked to allow access to the their media inputs. Each browser handles this one slightly differently, and these models also changes over time, but suffice to say that the idea here is again – to balance privacy of the users and the usability of the service
Me? I’d rather rely on the security measures placed in browsers. These go through the scrutiny of lots of people who are all too happy to announce these security flaws. Software from vendors that is specific to communications? A lot less so.
And yes. This isn’t enough. WebRTC is the building block used to build an application. A lot of what goes to the security of the finished service will rely on the developers who developed the application – but at least they got a head start by using WebRTC.
Ads and WebRTC

There’s an angle that isn’t much discussed about WebRTC. And that’s the uses it finds in the ad business.
The Bad
Two main scenarios that I’ve seen here:
- Fingerprinting. You get better means to know more about who the user behind the browser is
- Serving ads themselves. Theoretically, you might be able to serve ads via WebRTC, and that at the moment has the potential to circumvent ad blockers
The Good
There’s the second part of it. When ads are served today, the companies paying for these ads being served like to get their ROI. On the other hand, there are those who would like the money spent on ads to be wasted. So they use bots to click ads. Probably by automating selenium processes.
This is similar in concept to the “I am not a robot” type of entry measures and captchas out there. WebRTC gives another layer of understanding about the user and its behavior – and enables us to know if he is a human or a bot inside that browser. And yes. We can use it for things other than ad serving.
Where do we go from here?
There are two main approaches to security:
- Security by obscurity – relying on people not knowing the protocol in place. It works great when you’re small and insignificant, so no one is going to care about you anyway. It falls apart when you become popular
- Kerckhoffs’ principle – a system needs to be secure even when we know everything about the system. It works best when many people scrutinize, analyze and try to hack such systems, making it better and more robust through time
WebRTC is in the second category (the first one – security by obscurity – is often criticized for being unsecure by nature).
With all the resources put into WebRTC from all angles, security is also being taken care of and not left behind.
WebRTC is safe to adopt as developers. IT and security people in the enterprise shouldn’t shy away from it either – just make sure the vendor you pick did a decent job with his implementation.
Are you doing what it takes to improve the security of your WebRTC application?
If you are after a more thorough look at the topic, make sure to also read this article: Everything you need to know about WebRTC security.

Great, great, great piece! Maybe one of your best. Thanks Tsahi
Now look what you did Michael – I am all blushing…
Thanks for the kind words.
I wonder if the weakness of WebRTC is in its standardized communication. may attacker exploit weakness on multiple systems at once.
Nachliel,
I am not sure I understand the question, or how is weaknesses in WebRTC any different than weaknesses in other web and operating system technologies.